Quantum computing is developing rapidly. To cope with the threat of quantum computing being able to break the traditional cryptography currently in use in seconds, the US NIST has formulated a plan to transition to post-quantum cryptography to cope with the threat of quantum computing, requiring the industry to prepare all relevant systems and products for migration to the PQC algorithm in advance. As a leading technology company dedicated to HTTPS automation, ZoTrus Technology has formulated a timetable for the readiness of post-quantum cryptography HTTPS encryption full ecosystem products, taking practical actions to help customers easily complete the migration of anti-quantum algorithms.
1. What is quantum computing, quantum cryptography, post-quantum cryptography?
Quantum computing is a new computing mode that follows the laws of quantum mechanics to control quantum information units for computing. Unlike traditional computing, quantum computing follows the laws of quantum mechanics and is a new computing mode that can break through the bottleneck of traditional computing power. Quantum computer, as devices that perform quantum computing tasks, use quantum bits (qubits) as basic computing units. In quantum computing, based on the principle of quantum superposition, different states of quantum bits can be stored and processed simultaneously. The incredible and rapidly growing power and capabilities of quantum computing have changed the way we use computers to solve problems, analyze information, and protect data. Quantum computing opens the door to solving variability with huge nuances in non-traditional ways, and scientists see opportunities to gain huge benefits in highly complicated systems involving seemingly random factors, such as weather modeling, medicine and chemistry, finance, business and supply transportation, cybersecurity, quantum physics, and true artificial intelligence that Quantum computing can open up a whole new field of nuance and complexity for thinking machines in the application of artificial intelligence and machine learning.
Quantum Cryptography is the use of the unpredictability of quantum computing to encrypt and decrypt data, with information encoded directly in the qubits themselves. The most common quantum encryption uses the properties of qubits to secure data, which will produce qubit errors if someone tries to decrypt the information without permission. This form of quantum encryption works more like an alarm sensor on a door or window, which will raise an alarm if there is unauthorized access.
Post-Quantum Cryptography (PQC) is a mathematical cryptographic system that can be implemented on existing computers and resist future quantum computer attacks. Its algorithm is based on mathematical problems that are difficult to crack with quantum computing, such as lattice cryptography, multivariate polynomials, and coding theory, and can be compatible with existing systems through hybrid encryption mechanisms. In PQC, mathematics uses quantum properties to create equations that are difficult to solve, and even quantum computers cannot "skip" to the correct solution. One of the benefits of PQC is that it is based on highly unsolvable equations. Because its basic structure is the same as current traditional cryptography, it can be deployed using methods like current state-of-the-art encryption, running seamlessly with today's protocols and network systems, and can protect most of today's systems.
While quantum computers are still in their infancy, cybersecurity experts and cryptographers have already created quantum-safe algorithms that can prevent attacks. These security algorithms will continue to evolve as quantum computing advances, but current protections can stay ahead of the quantum threat when implemented correctly. Although truly functioning quantum computers may be years away, attackers may adopt a "harvest now, decrypt later" approach to counter the threat, collecting and storing encrypted state data first, and then decrypting the stored data encrypted by traditional cryptography once quantum computers are available. This is why it is urgent to transition to post-quantum cryptography as soon as possible to protect important data from all forms of current and future attacks, whether using traditional computers or future quantum computers.
2. Global PQC standard development status and migration timeline
The US National Institute of Standards and Technology (NIST) released three PQC standards in August 2024 to begin the next important phase of the transition to post-quantum cryptography: (1) FIPS 203 - Module-Lattice-Based Key-Encapsulation Mechanism, ML-KEM, (2) FIPS 204 - Module-Lattice-Based Digital Signature Algorithm, ML-DSA, (3) FIPS 205 - Stateless Hash-Based Signature Algorithm, abbreviated as SLH-DSA.
Among the three PQC standards, FIPS 204 and 205 are quantum-resistant digital signature algorithms, and FIPS 203 is a quantum-resistant key encapsulation algorithm. The existing digital signature algorithms ECDSA, RSA, EdDSA, and key encapsulation algorithms based on ECC and RSA algorithms are all easily cracked by quantum computers, but the existing symmetric encryption algorithms are not easily cracked by quantum computers.
In November 2024, NIST released a draft for public comments on NIST IR 8547 "Transition to Post-Quantum Cryptography Standards". The report describes NIST's expected approach to transitioning from cryptographic algorithms vulnerable to quantum attacks to post-quantum digital signature algorithms and key establishment schemes, identifies existing cryptographic standards vulnerable to quantum attacks and quantum-resistant cryptographic standards to which information technology products and services need to transition, and aims to promote cooperation with industry, standards organizations, and related institutions to promote and accelerate the adoption of post-quantum cryptography. NIST believes that it may take 10 to 20 years from algorithm standardization to full integration into information systems. This timetable reflects the complexity of the industry building algorithms into products and services, procuring these products and services, and integrating these products and services into technical infrastructure. NIST has released a transition timetable for the migration of traditional cryptographic algorithms to PQC standards, with the goal of mitigating as much of the quantum risk as is feasible by 2035. The traditional cryptographic algorithms RSA-2048 and ECC-256, which are currently in widespread use, will be deprecated in 2030 and disallowed in 2035. That is, the comprehensive PQC migration of all systems, products and services must be completed by 2035.
The UK National Cyber Security Center (NCSC) released a timeline for post-quantum cryptography migration in March 2025 , requiring discovery and assessment to be completed by 2028, a preliminary migration plan to be developed, high-priority PQC migration to be completed by 2031, and full PQC migration of all systems, products and services to be completed by 2035 to ensure that encryption security remains robust in the face of future threats. NCSC warned that PQC migration is inevitable and urged governments and businesses to plan early, coordinate with suppliers, and implement protocol testing to ensure a smooth and secure transition.
The EU published a PQC migration roadmap and timetable in June 2025, recommending that all member states launch national PQC migration strategies by the end of 2026 at the latest and coordinate related efforts at the EU level. And high-risk application scenarios should move to PQC as soon as possible, no later than the end of 2030. Thereafter, quantum security upgrades should be enabled by default and the PQC migration plan should be improved. By 2035, as many system PQC migrations as possible should be completed. At the same time, when moving to post-quantum cryptography solutions, it is recommended to use standardized and tested hybrid algorithm solutions as much as possible.
China has not yet released a detailed PQC migration schedule, and prefers to independently develop post-quantum cryptographic algorithms rather than directly adopt NIST standard algorithms. However, the products being researched by major cryptographic manufacturers are basically hybrid key encapsulation mechanism applications and digital signature applications based on the existing SM2 algorithm plus the three PQC standards formulated by NIST.
3. ZoTrus is building a PQC HTTPS encryption application ecosystem
ZoTrus Technology has been committed to dual-algorithm SSL certificate automation management solutions, and it is also developing seamless migration to quantum-resistant algorithm HTTPS encryption solutions based on traditional algorithm HTTPS encryption automation management solutions. To this end, ZoTrus Technology is building a full ecosystem of post-quantum cryptographic HTTPS encryption products, as shown in the figure below, including the following seven products and services: ZT Browser that supports the PQC algorithm, ZoTrus HTTPS Automation Gateway that supports the PQC algorithm, ZoTrus PQC HSM (including the PQC root CA certificates) for generating PQC root CA certificates and keys, ZoTrus PQC CA System for issuing PQC algorithm SSL certificates, ZoTrus PQC ACME Service System for providing certificate automatic management services for PQC algorithm SSL certificates, ZoTrus PQC Certificate Transparency Log for providing certificate transparency services for PQC algorithm SSL certificates, and ZoTrus PQC algorithm SSL certificates with hybrid algorithm SSL certificates.
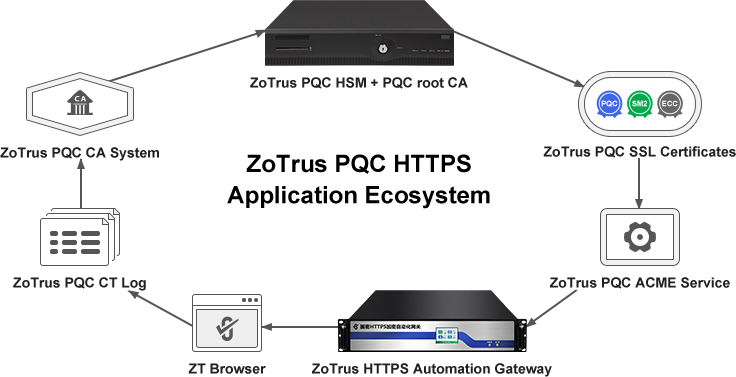
Based on the internationally agreed timetable for post-quantum cryptography migration, ZoTrus Technology has developed a timetable for the readiness of the entire ecosystem of post-quantum cryptography HTTPS encryption applications, which will be completed in 7 steps.
The specific product readiness of each step is as follows:
- By December 2025, ZT Browser and ZoTrus Gateway will support ECC+MLKEM and SM2+MLKEM dual-algorithm hybrid key encapsulation mechanisms to achieve hybrid PQC algorithm HTTPS encryption.
- By March 2026, ZoTrus CA will create ECC+MLDSA and SM2+MLDSA dual-algorithm hybrid root CA certificates and sub-CA certificates for issuing PQC hybrid algorithm SSL certificates.
- By September 2026, ZT Browser and ZoTrus Gateway will support dual-algorithm PQC hybrid algorithm SSL certificates and adaptive 4 algorithms to implement PQC algorithm HTTPS encryption.
- By December 2026, ZoTrus CA will create pure PQC algorithm (ML-DSA) root CA certificate and sub-CA certificates for issuing pure PQC algorithm SSL certificates.
- By July 2027, ZT Browser and ZoTrus Gateway will support pure PQC algorithm SSL certificates to implement PQC algorithm HTTPS encryption.
- By December 2028, ZT Browser and ZoTrus Gateway will support China PQC algorithm SSL certificates to implement China PQC algorithm HTTPS encryption.
- By December 2029, ZoTrus Technology will have completed the development of a full ecosystem of HTTPS encryption PQC algorithm products, supporting international and China PQC algorithms, and helping customers achieve seamless PQC HTTPS encryption migration.
4. Act now to prepare for seamless migration to PQC HTTPS encryption
HTTPS technology is experiencing two technological revolutions. The first is the technological revolution of "SSL certificate management from manual to automatic management" which must be completed before March 15, 2026, and the second is the technological revolution of "HTTPS encryption from traditional cryptography to quantum-resistant cryptography" which must be completed before December 31, 2029. The full line of PQC HTTPS encryption products developed by ZoTrus Technology is planned to be completed in December 2029 to help customers complete the migration of HTTPS encryption to post-quantum in a timely manner.
As Google Chrome listed in its "Move Forward, Together" plan, one of the six benefits of implementing automatic SSL certificate management is "easy transition to quantum-resistant algorithms." The ultimate goal of the technological revolution of “continuously shorten the validity period of SSL certificates” is to resist quantum attacks, because current cryptographic algorithms cannot resist the upcoming quantum computing. The main purpose of continuously shortening the validity period of SSL certificates is to achieve automatic updates of SSL certificates, provide technical means for automatic updates to support post-quantum cryptographic algorithms, and ensure seamless transition to quantum-resistant algorithms when conditions are ripe. The ultimate goal of the SSL certificate automation technology revolution is still to quantum-resistant technology revolution.
The ultimate goal of the first technological revolution is to easily realize the second technological revolution. ZoTrus Technology has launched a client-to-cloud dual-algorithm SSL certificate automation management solution, which innovatively realizes that one micro-transformation can easily complete the necessary technical transformations for the two technological revolutions. For users, since both technological revolutions are necessary, choose to complete them at once, and make technical preparations for seamless migration to post-quantum cryptography HTTPS encryption, so that the subsequent migration of HTTPS encryption to post-quantum cryptography can be completed smoothly and with assurance.
5. Embrace and easily complete the PQC revolution
Since it may take several years for a truly functional quantum computer to arrive, it is not too late to start working on it now. Work mainly needs to be carried out in the following three areas.
First, the organization must be prepared by understanding its data assets, where those assets are stored, and the flow of sensitive data in the environment. Organizations should consider taking steps to tag data based on sensitivity and business importance, as well as the lifecycle of the data. It is important to manage data and understand where it is backed up, while considering storage data protection best practices such as deduplication and offsite backups. And compliance, record retention, and legal hold considerations should be considered to ensure that the data is appropriately managed according to each set of requirements. If the value of the data exceeds its lifecycle, or if record retention requirements require the data to be deleted, data destruction should be incorporated into the planning process for how the data will be handled.
Secondly, the organization must fully understand which systems in the organization currently implement HTTPS encryption and which systems have not yet implemented it. The organization must fully implement HTTPS encryption for all systems and fully implement automatic management of SSL certificates, whether for internet or intranet systems. In order to respond to the data security threat of "harvest now, decrypt later", the organization must enable post-quantum hybrid HTTPS encryption as soon as possible while continuing to use traditional cryptographic SSL certificates to minimize the possibility that ciphertext data is stored now and decrypted later.
Third, develop a migration plan. After post-quantum cryptographic products are available, quantum cryptography migration must be completed as soon as possible, with HTTPS encryption migration given priority, followed by PQC migration of digital signatures and encryption of data, giving priority to the most sensitive and critical data assets.
Finally, please remember that ZoTrus Technology has started and partially completed the research and development of post-quantum cryptography full-ecosystem products to help customers protect the security of digital assets. ZoTrus post-quantum cryptography HTTPS encryption automation management solution is constantly being improved, and will successively launch PQC email encryption automation solutions, document PQC digital signature and encryption solutions, and software code PQC digital signature solutions. ZoTrus actively cooperates with the global industry to actively develop innovative solutions to shape a common PQC future and help customers easily complete PQC migration smoothly.