Document security requires one-click automation to realize document digital signature, encryption and time stamp!
For document security, what you need is a document signing service, not a document signing certificate! ZoTrus Technology document security solution provides the cryptographic services you really need, with one-click automation to achieve document digital signature, encryption and timestamp. Not upload the user's document to be signed to ensure the security of the confidential information of document. All signed documents are dual algorithm and dual timestamp, with global trust and cryptography compliance.
-
1
One client with multi-purpose, browsing and reading.
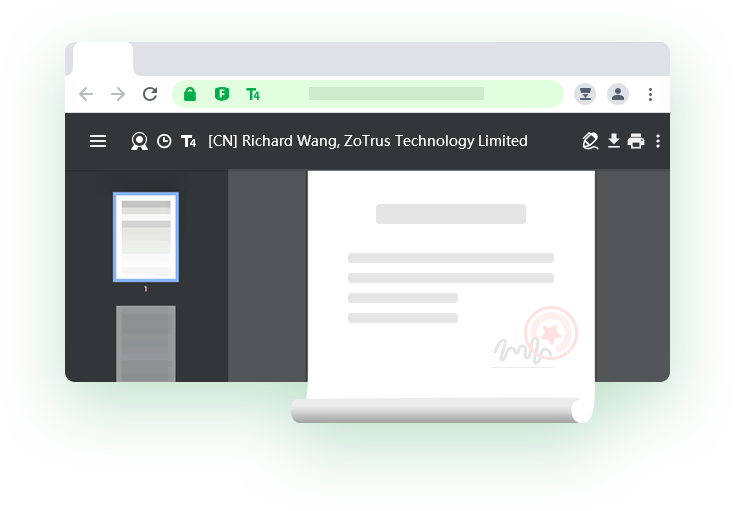
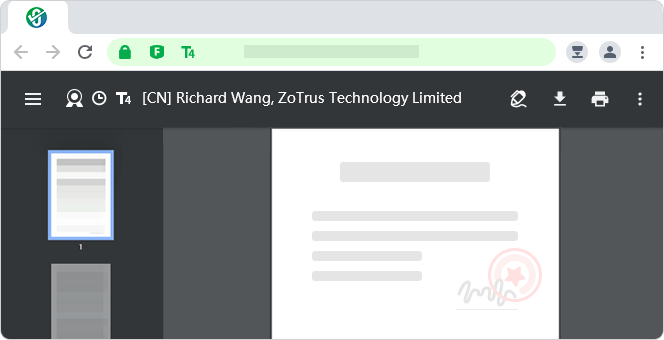
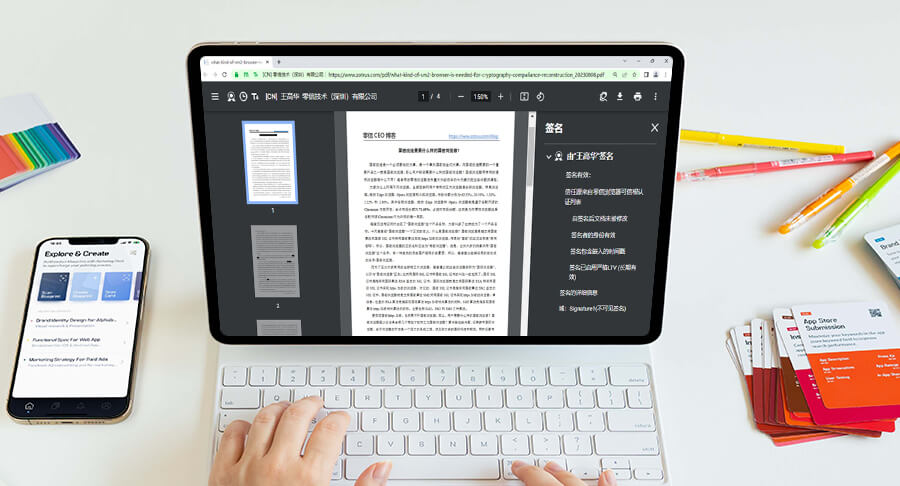
ZT Browser integrates a PDF reader to seamlessly and quickly load and view PDF documents when browsing the web, without the need to install additional PDF reader software. Real-time verification of document digital signatures, real-time display of the document's trusted identity, enhanced user trust and protection from fake identity documents. -
2
Client-Cloud integration, automatic digital signing.
"One Client” (ZT Browser) and "One Cloud" (ZoTrus Cloud Cryptographic Infrastructure) are integrated, innovatively realize automatic document digital signature and encryption services, realize zero trust security of documents, and solve the problem of "Client only" or "Cloud only” cannot solve the automatic digital signature technical problems. -
3
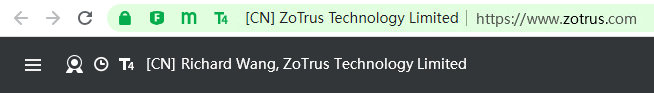
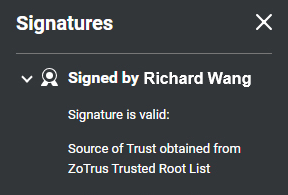
Global trust, cryptography compliance.
Comply with the Cloud Signature Consortium (CSC) standard to implement cloud document signing services, follow international standards and global trust. The cloud signing certificate is publicly trusted, and Adobe Reader trusted. Automatically configure the SM2 algorithm document signing certificate for end users, follow the China cryptographic standard, and trusted by ZT Browser to meet the user's cryptography compliance needs. -
4
Protect privacy and business secrets.
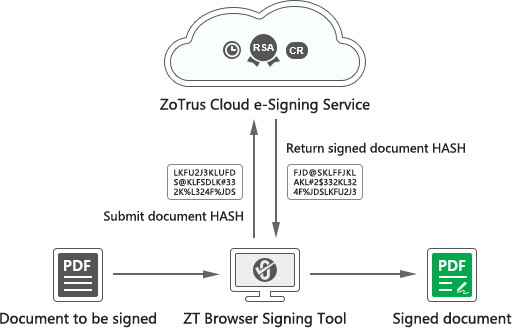
The document to be signed is not uploaded to the cloud, but the HASH data of the document to be signed is submitted to the ZoTrus Cloud Signing Service System. The cloud system only completes the HASH data signature and timestamp signature, then returns the signed data to the ZT Browser. ZT Browser completes the document signing on the local computer, which effectively protects the personal privacy and business secrets of user documents. -
5
Purchase on demand, worry-free signing.
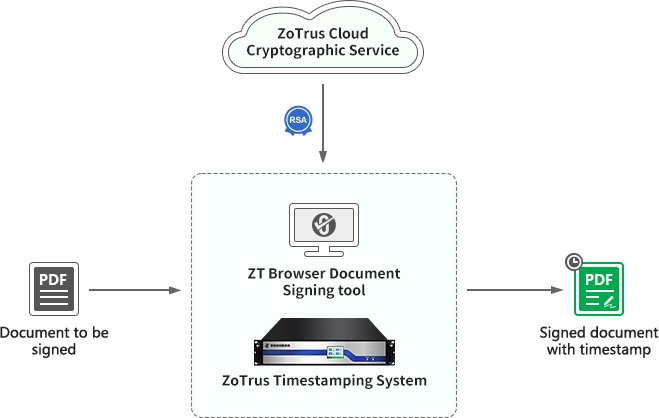
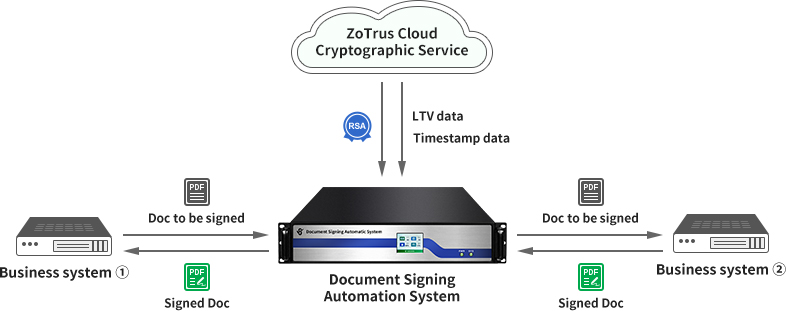
Charges are based on the number of signed documents and can be purchased on demand, with discounts for large quantities. You only need to purchase the signing service, and there is no need to apply for, install, renew signing certificate every year, achieving worry-free document signing. The number of purchased signatures is always valid and there is no time limit. Every time a document is signed, the timestamp signature and LTV data are automatically countersigned, ensuring that the digital signature of the signed document is valid for a long time. -
6
Optional document encryption service.
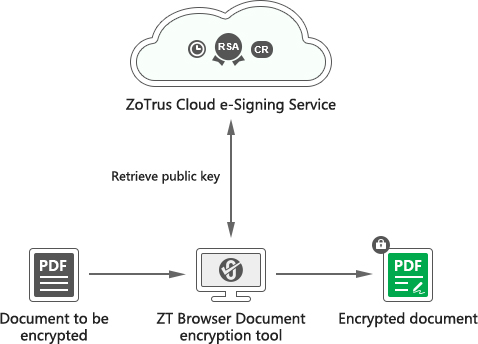
When users digitally sign a document, they can choose the document encryption service. Selecting the buddy in their address book who has the right to read the document, the document will be automatically encrypted with the buddy's public key. Only this buddy can use their private key to automatically and seamlessly decrypt and read the document. This encrypted document cannot be opened by anyone else. This is the most effective protection of confidential documents. Users can choose the free service and paid value-added services.